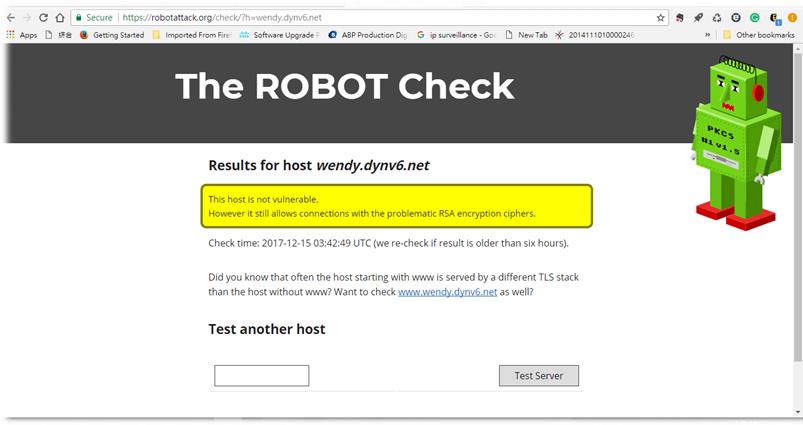
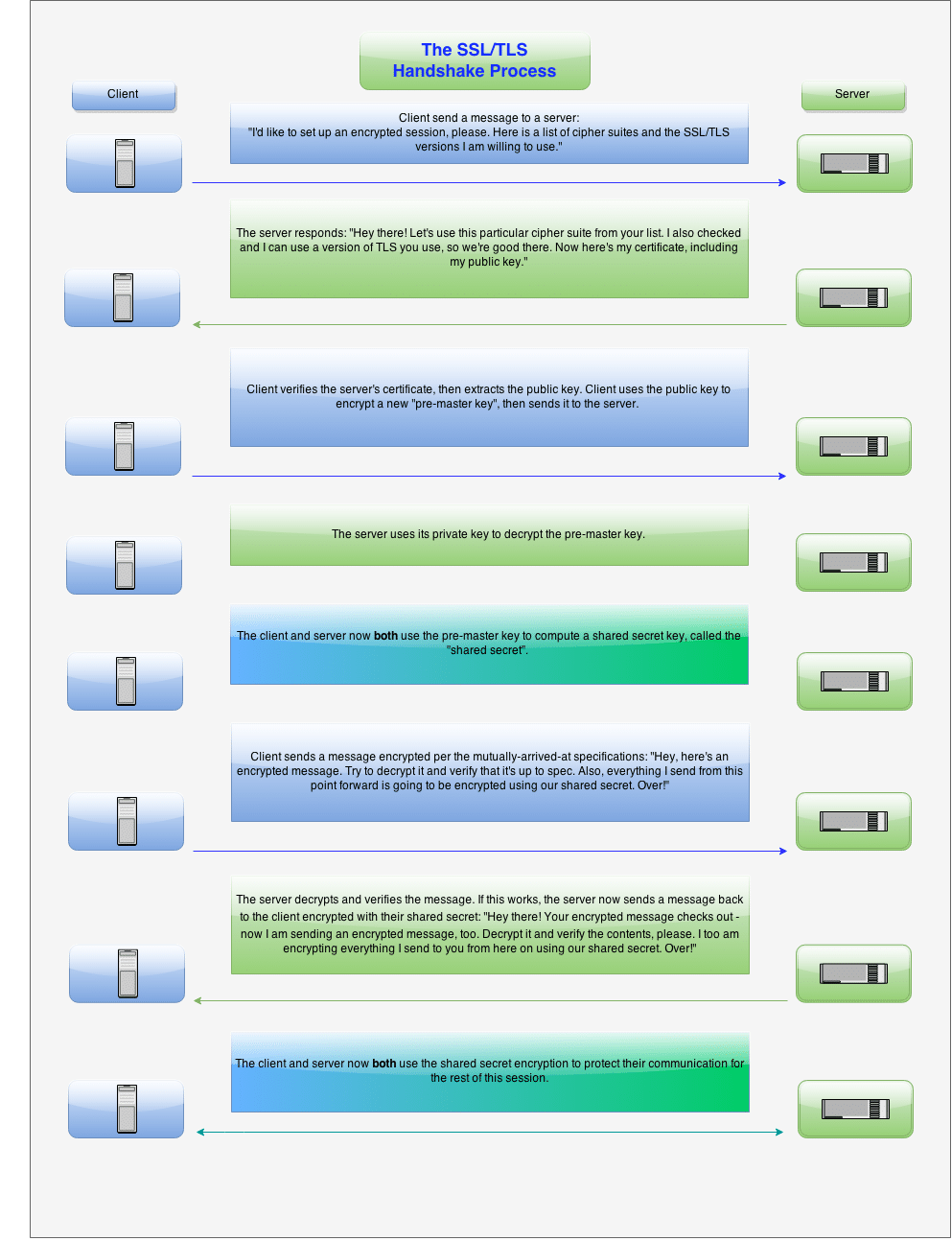
ROBOT Attack: RSA TLS crypto attack worked against Facebook, PayPal, and tens of 100 top domainsSecurity Affairs
![Heromice #2: Robot Attack [Paperback] [Jan 01, 2013]: Geronimo Stilton: 9789351033738: Books: Amazon.com Heromice #2: Robot Attack [Paperback] [Jan 01, 2013]: Geronimo Stilton: 9789351033738: Books: Amazon.com](https://images-na.ssl-images-amazon.com/images/I/51kfV4sGUdL.jpg)
Heromice #2: Robot Attack [Paperback] [Jan 01, 2013]: Geronimo Stilton: 9789351033738: Books: Amazon.com

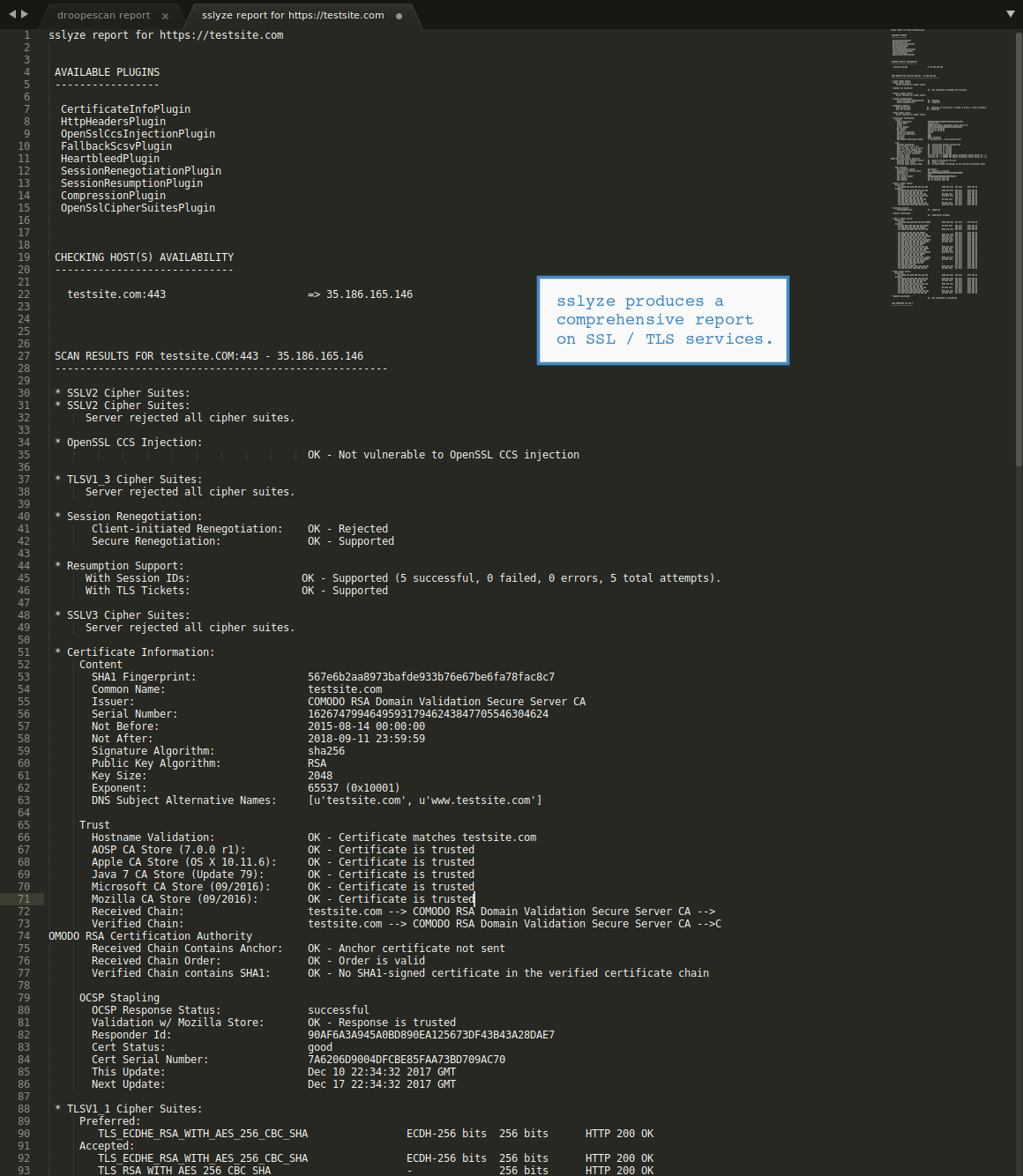
sslyze v2.0 releases: Fast and powerful SSL/TLS server scanning library | by Anastasis Vasileiadis | Medium
![The ROBOT Attack: RSA Encryption Is Vulnerable – Choose ECC in TLS/SSL Certificates to Ensure Security [Article] - TRUSTZONE The ROBOT Attack: RSA Encryption Is Vulnerable – Choose ECC in TLS/SSL Certificates to Ensure Security [Article] - TRUSTZONE](https://trustzone.com/wp-content/uploads/2020/06/hero-illustration-knowledge-texts-01.png)
The ROBOT Attack: RSA Encryption Is Vulnerable – Choose ECC in TLS/SSL Certificates to Ensure Security [Article] - TRUSTZONE
![The ROBOT Attack: RSA Encryption Is Vulnerable – Choose ECC in TLS/SSL Certificates to Ensure Security [Article] - TRUSTZONE The ROBOT Attack: RSA Encryption Is Vulnerable – Choose ECC in TLS/SSL Certificates to Ensure Security [Article] - TRUSTZONE](https://trustzone.com/wp-content/uploads/2020/07/TRUSTZONE-logo.png)